I lost my MacBook Air this week. Luckily, I got it back when somebody transformed it into the chief of the eatery where I left it.
I was blessed, yet imagine a scenario where the discoverer chose to be a manager. Imagine a scenario where she additionally figured out how to break my framework secret key, get to my email, bank site, and other individual subtleties that I have on the framework. I'd be in a bad way since I didn't do some extremely basic things. I did a couple of things right, yet ought to have accomplished more.
Ensure you gain from my disappointment and don't fall prey to the unscrupulous individuals out there. I lucked out, however you may not.
Here are a couple of ways you can keep your MacBook, or Windows note pad, secured, and even track it down on the off chance that it disappears. The best part is that you don't need to spend a dime to do this.
Prey Tacking Software
This late spring our manager Josh Smith posted about his utilization of LoJack for Laptops, a PC following application that causes you recuperate your PC whenever taken or lost. That arrangement will make sure about your PC at a cost. A free elective he referenced originates from the people at the Prey Project. I picked it since I'm modest, yet it additionally will let me include highlights at a good cost.

Like LoJack, Prey keeps you shielded from corrupt individuals who gain admittance to your framework. Pursue a record and introduce the product on your Mac, Windows, Unbuntu or other Linux framework and it runs unobtrusively out of sight. Indeed, you won't have the foggiest idea about its running. That is something worth being thankful for since the trouble makers won't know it either. On my Mac it doesn't have a menu bar symbol or an application symbol in the Applications envelope.
You can watch the organization's video demo for the Pro plans which do cost somewhere in the range of $5/month for an individual record up to $399/month for big business clients with a huge number of PCs to secure. You can utilize the administration for nothing if all you need is extremely fundamental following. Included highlights incorporate establishment more PCs, a functioning mode that monitors your PC constantly, not exactly what you report it, and a couple of more highlights which you can see on their arrangements page. They additionally have applications that work for iPhone (in beta and will be discharged soon) and Android.
Prey Project presentation from Carlos Yaconi on Vimeo.
iCloud Find My Mac
For Mac clients, the prospective iCloud will offer another help especially like the Find My Phone for iOS. It will follow your PC and let you know where it was keep going utilized dependent on where the miscreants sign onto the Internet. The component will be all set for all clients on October 12 when iCloud dispatches and offers a free form with up to 5GB of document stockpiling and other paid variants with included capacity. Utilize the capacity to reinforcement and sync records among Macs and iOS gadgets.
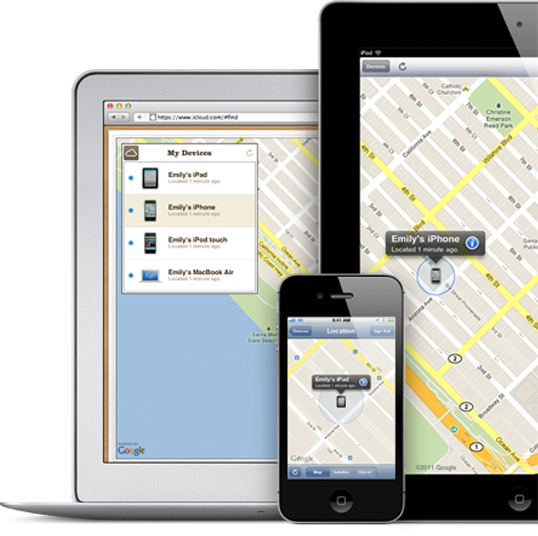
The key security include finds your Mac on a guide (see picture above). It will likewise let you make an impression on the PC with the goal that you can tell the individual who "found" your PC that you need it back and how they can make the best choice and transform it into you. On the off chance that you have to you can secure the framework and remote wipe the client information in your Home organizer.
These arrangements may work incredible, yet imagine a scenario where you lose it and nobody discovers it for sure in the event that it you, another person or the compelling force of nature annihilates it. Imagine a scenario where the trouble makers recognize what she's doing and wipes the framework before any of these security applications can kick in. You have to do a couple of things to secure your information. You ought to be following these prescribed procedures in any case.
Back Up Your Data
Have a normal reinforcement plan. On the off chance that I hadn't recuperated my MacBook, in any event I'd in any case have the entirety of my reports and records. That is on the grounds that I use SugarSync to synchronize my significant documents between my three PCs and their distributed storage administration. I additionally consistently keep a reinforcement duplicate of the entirety of my music, recordings, and pictures. I reinforcement the media documents physically since they occupy an excessive amount of room for SugarSync to deal with (over 200GB). Each time I download new music, make another video or burden new photographs onto my PC, I back them up to my 2TB Firewire drive snared to my other PC.
iCloud will prove to be useful for Mac clients since it additionally handles document reinforcement/matching up. Windows clients can exploit SugarSync, DropBox, or Windows Live Skydrive, just to give some examples. Whatever you decide to utilize, use it! For boundless information reinforcement progressively, get a Carbonite account.
Password Protection
- Passwords ensure you just on the off chance that you do the accompanying:
- Make great passwords including irregular numbers, letters (the two tops and lowercase) and if conceivable accentuation marks
- Try not to utilize regular words, names, notable individual information like birthday celebrations
- Utilize various passwords for the entirety of your destinations – don't have one secret phrase to administer them all
- Utilize a secret word database application like Lastpass
The last proposal can truly help in the event that you secret phrase secure your Lastpass account with a great secret phrase. At that point, you just need to recollect one secret key. Lastpass stores your secret word database online in encoded structure with the goal that not even they realize what the passwords are. They additionally don't have the foggiest idea about your secret phrase, so you ensure you make a decent one yet additionally recollect it. View the Lastpass guidance video beneath:
At long last, don't keep your passwords recorded close to your PC. In the event that you have little scratch pad with the entirety of your passwords in your PC sack, at that point you are simply requesting to have your ledger exhausted by a crook.
Lock It Down
At long last, recollect that your PC can be taken regardless of whether you simply go over the space for a top off or to the bathroom for a pitstop. A decent lock can help, similar to a Kensington lock or Griffin's TechSafe Calbe Lock that I as of late reviewed.This framework doesn't work with the MacBook Air, yet on the off chance that you don't have a Kensington lock space on your PC, this is a decent arrangement.

With these you lock your PC to the table or some overwhelming item and the get and-go criminal will be obstructed from taking your PC.



























